Browse Resources
Computer science -- Security and privacy
Resources | |
|---|---|
From the University of Maryland, this page presents materials from the course Cybersafety, Cyberethics and Cybersecurity (C3) for Educators: Ethical and Legal Implications for Classroom Technology. Taught by Davina Pruitt-Mentle for graduate and undergraduate students alike, this course "addresses...
The Government Accountability Office (GAO) issued this eighty-six page report in November 2011 to address the threats to federal government information systems and infrastructures. In order to remedy this problem, the GAO assessed the existing workplace initiatives in the federal government for...
This three dimensional world map, from Kaspersky Lab, shows threats to cyber security in real time. Separate colors indicate detection categories, including web anti-virus and intrusion detection scans, and each nation can be selected to view overall threat statistics and rankings. The map can be...
Program Description:
River Valley Community College, in association with Program Development in Cybersecurity with Focus on Business and Healthcare Concepts, has developed a 4-semester program to prepare students to working the Information Assurance (IA) field with a focus on Cybersecurity and...
Program Description:
River Valley Community College, in association with Program Development in Cybersecurity with Focus on Business and Healthcare Concepts, has developed a 4-semester program to prepare students to working the Information Assurance (IA) field with a focus on Cybersecurity and...
Program Description:
River Valley Community College, in association with Program Development in Cybersecurity with Focus on Business and Healthcare Concepts, has developed a 4-semester program to prepare students to working the Information Assurance (IA) field with a focus on Cybersecurity and...
This PDF document, provided by the Ohio Region Cybersecurity Technician Training Pipeline at Columbus State Community College, outlines a job description for an entry-level cybersecurity technician. The document lists the various roles that these professionals play and provides the corresponding...
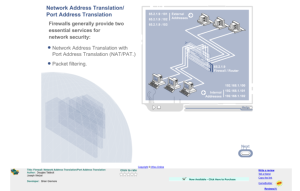
This brief interactive activity, by Electromechanical Digital Library and Wisconsin Technical College System faculty members Joseph Wetzel and Douglas Tabbutt, provides a basic lesson on firewalls. This learning activity introduces the purpose of a firewall and a simple overview of what a firewall...
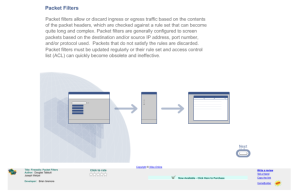
This brief interactive activity, by Electromechanical Digital Library and Wisconsin Technical College System faculty members Joseph Wetzel and Douglas Tabbutt, provides an interactive lesson on packet filters to demonstrate their use. After a brief explanation, there is an activity that allows the...
Gordon and Mike's ICT Podcast offers perspectives on the information and communication technologies (ICT) industries from Gordon Snyder and Mike Qaissaunee. In this podcast, Gordon and Mike are joined by Sam Browne from City College of San Francisco. The trio discuss the case of a man who tracked...
| |
| ← Previous | Next → |